Data vs. Metadata
Google uses HTTPS for all search queries. That’s good, because it means that all of the questions you ask (a.k.a. your data) will be encrypted. However… regardless of HTTPS, inferences about your searches can still be made by somebody with access to your network traffic. For example:
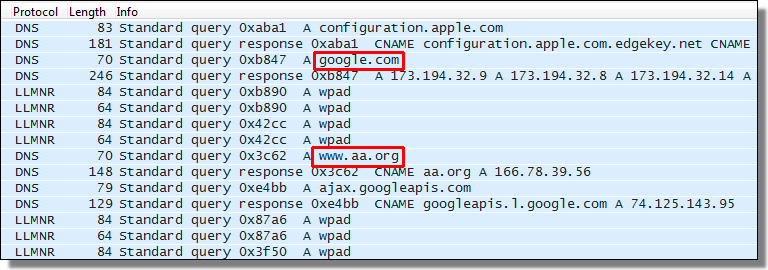
In the screenshot above, a popular “packet analyzer” displays DNS queries (a.k.a. metadata). We first connected our test device to google.com and performed a search — and then we clicked on the top search result link — and connected to aa.org.
The deductive reasoning skills of Sherlock Holmes aren’t required to figure out “alcoholics anonymous” was searched for. And even if aa.org used HTTPS encryption (it doesn’t), using DNS metadata, we can still infer the contents of the search data. The connections made offer all the evidence needed.
And that’s why metadata matters.
via: http://www.f-secure.com/weblog/archives/00002736.html
Kali Tools Site Launched
A new Kali Linux Tools website has been implemented, with well documented Kali Linux Tool Listing contains package descriptions, tool homepage links and usage examples.
Kali Linux contains a large amount of tools from various different niches of the security and forensics fields. This site aims to list them all and provide a quick reference to these tools.
Password Cracking for noobs: All your hashes are belong to us
As the great philosopher ludacris said, “if you get hashes, you crack them. it’s a rule.” Welcome to a world where getting a hash should mean you also just owned that account. This is boring if it’s your grandmother’s computer, but way more interesting when it’s a bank. This talk will discuss the basic concepts behind password hashes, how they can be obtained, and what to do with them once you have them. Special attention will be given to demos related to effective hash cracking techniques and introduction to toolsets for making the process as efficient and effective as possible.
Bash commands for Kali:
mkdir NTLM-Project && cd NTLM-Project wget http://www.alexrams.com/blog/wp-content/uploads/2014/09/sorted.zip unzip sorted wget http://www.alexrams.com/blog/wp-content/uploads/2014/09/hashes.txt john --crack-status --rules --format=nt2 --wordlist=sorted.txt hashes.txt cd ~/.john cat john.pot
- local: hashes.txt
- local: sorted.zip
- remote: www.lockfale.com/sorted.zip
hacking 80211 basics
Benjamin Hussein Smith (thex1le) at Defcon Wireless Village 2014 talks about Hacking 802.11 Basics / for Beginners. Here is a list of terms uesd within the video: Wireless Term List.