A zone transfer in DNS is a normal occurrence, but when this information falls into the wrong hands the effect can be devastating. A zone transfer is designed to update DNS servers with the correct information; however, the zone contains information that could map out the network, providing valuable data about the structure of the environment.
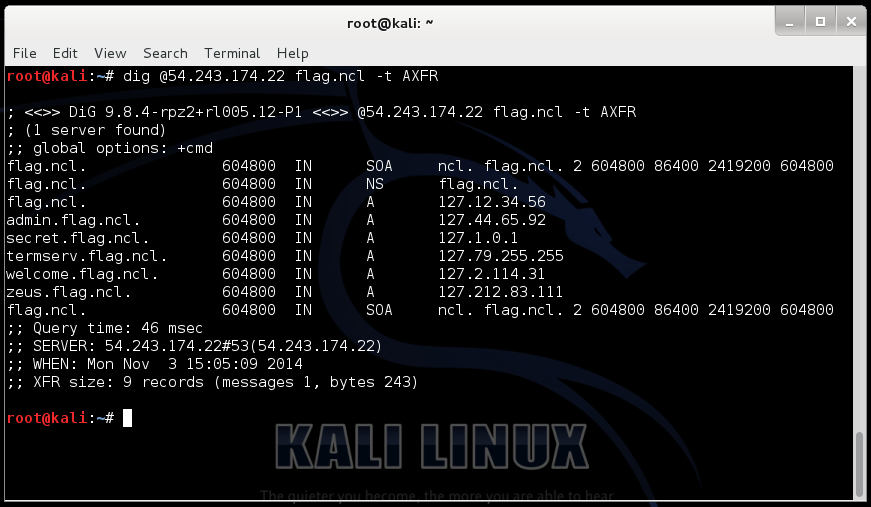
The screenshot above shows the dig command to contact the name server on 54.243.174.22, asking for information about a domain called “flag.ncl” and there is also a zone transfer being invoked with “-t AXFR”. As you can see from the output there is a good deal of information about potential target systems in the flag.ncl domain.
dig @54.243.174.22 flag.ncl -t AXFR
; <<>> DiG 9.8.4-rpz2+rl005.12-P1 <<>> @54.243.174.22 flag.ncl -t AXFR
; (1 server found)
;; global options: +cmd
flag.ncl. 604800 IN SOA ncl. flag.ncl. 2 604800 86400 2419200 604800
flag.ncl. 604800 IN NS flag.ncl.
flag.ncl. 604800 IN A 127.12.34.56
admin.flag.ncl. 604800 IN A 127.44.65.92
secret.flag.ncl. 604800 IN A 127.1.0.1
termserv.flag.ncl. 604800 IN A 127.79.255.255
welcome.flag.ncl. 604800 IN A 127.2.114.31
zeus.flag.ncl. 604800 IN A 127.212.83.111
flag.ncl. 604800 IN SOA ncl. flag.ncl. 2 604800 86400 2419200 604800
;; Query time: 46 msec
;; SERVER: 54.243.174.22#53(54.243.174.22)
;; WHEN: Mon Nov 3 15:05:09 2014
;; XFR size: 9 records (messages 1, bytes 243)
Question and Answers for (Enum 2) Enumeration and Exploitation:
What is the IP Address for the domain: “flag.ncl”?
127.12.34.56
What is the domain name with the IP Address of 127.44.65.92 (FQDN)?
admin.flag.ncl
What is the domain name with the IP Address of 127.212.83.111 (FQDN)?
zeus.flag.ncl
What is the domain name with the IP Address of 127.2.114.31 (FQDN)?
welcome.flag.ncl
What is the domain name with the IP Address of 127.79.255.255 (FQDN)?
termserv.flag.ncl
What is the domain name with the IP Address of 127.1.0.1 (FQDN)?
secret.flag.ncl
Common DNS Record Types and Their Use:
A (address)
Maps a host name to an IP address
SOA (Start of Authority)
Identifies the DNS server responsible for the domain information
CNAME (canonical name)
Provides additional names or aliases for the address record
MX (mail exchange)
Identifies the mail server for the domain
SRV (service)
Identifies services such as directory services
PTR (pointer)
Maps IP addresses to host names
NS (name server)
Identifies other name servers for the domain




